N10-007 Explain the importance of implementing network segmentation
SCADA systems/Industrial control systems
SCADA (supervisory control and data acquisition) is an industrial control system at the core of many modern industries such as manufacturing, energy, water, power, transportation and many more. SCADA systems deploy multiple technologies that allow organizations to monitor, gather, and process data as well as send commands to those points that are transmitting data. Virtually anywhere you look in today’s world, you will find some version of a SCADA system running, whether it’s at your local supermarket, refinery, waste water treatment plant, or even your own home.
SCADA systems range from simple configurations to large, complex projects. Most SCADA systems utilize HMI (human-machine interface) software that allows users to interact with and control the machines and devices that the HMI is connected to such as valves, pumps, motors, and much more.
SCADA software receives its information from RTUs (remote terminal units) or PLCs (programmable logic controllers) which can receive their information from sensors or manually inputted values. From here, the data can be used to effectively monitor, collect and analyze data, which can potentially reduce waste and improve efficiency resulting in savings of both time and money. Numerous case studies have been published highlighting the benefits and savings of using a modern SCADA software solution such as Ignition.
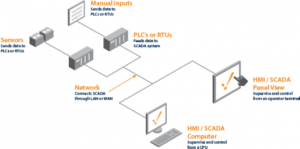
Modern SCADA Systems
Modern SCADA systems allow real-time data from the plant floor to be accessed from anywhere in the world. This type of access to real-time information allows governments, businesses and individuals to make data-driven decisions about how to improve their processes. These decisions would be either impossible or take substantial time and resources to complete without SCADA software. The introduction of modern IT standards and practices such as SQL and web-based applications into SCADA software has greatly improved the efficiencies, security, productivity and reliability of SCADA systems.
SCADA software that utilizes the power of SQL databases has a huge advantage over antiquated SCADA software solutions. One huge advantage of using SQL databases with a SCADA system is that it makes it easier to integrate into existing MES and ERP systems, allowing data to flow seamlessly through an entire organization. Historical data from a SCADA system can also be logged in a SQL database which allows for trending of data to make data analysis easier.
Ignition HMI/SCADA Software
Ignition by Inductive Automation® is a SCADA software platform that many businesses and organizations have switched to using. Ignition has been installed in thousands of locations in over 70 countries and has quickly become the go-to choice for HMI / SCADA software. Its powerful and robust nature allows SCADA system integrators to reach the demands of their customers while costing less than other SCADA software solutions. Because it uses modern IT practices, it is compatible with current SCADA system components, resulting in a more cost-effective approach while yielding higher results. Its pricing structure is unique in that users only have to pay a flat fee to use the software, which is server-based. Other SCADA vendors typically charge per client or per tag. Ignition allows users to launch unlimited clients and monitor unlimited tags.
Inductive Automation’s motto of “Dream it. Do it.” is a perfect embodiment of what Ignition can do. While many people think that the software’ power and bold claims are too good to be true, one demonstration of what the software can do is all it takes to change their mind. Once they see what’s possible, they become believers and begin to dream how the software can fit their needs. If you are interested in seeing how Ignition can improve your organization, schedule a 30-minute demonstration with one of our reps or download the software for yourself and see what you can accomplish.
Legacy systems
A legacy system is not necessarily defined by age. Legacy may refer to lack of vendor support or a system’s incapacity to meet organizational requirements. For example, a large mainframe may use a 64-bit Java, while a Linux platform might utilize code from the 1960s. Legacy conditions refer to a system’s difficulty (or inability) to be maintained, supported or improved. A legacy system is usually incompatible with newly purchased systems.
Legacy systems are high maintenance and may involve intricate patching and modifications. Porting techniques are often used for software adjustments or adaptation. Older hardware may require added compatibility layers to facilitate device functionality in incompatible environments.
An organization might continue to use legacy systems for a wide range of reasons, such as the following:
- “If it ain’t broke, don’t fix it!” The system might work adequately.
- The system is complex, and documentation is poor. Simply defining scope can be difficult.
- A redesign is costly, due to complexity or monolithic architecture.
Separate private/public networks
The simplest way you might think to offer public or guest Wi-Fi access is to let people on an existing Wi-Fi network used by the business, but this isn’t secure. Allowing outsiders on the private network could open your company up to hacking and data theft.
Private wireless networks should be encrypted with WPA2-Personal security, at least, to keep others from connecting and eavesdropping on your network traffic. Businesses with more than a handful of Wi-Fi users should consider using WPA2-Enterprise security, requiring a RADIUS server or service, to better secure and manage Wi-Fi access.
Businesses with existing private Wi-Fi network might be able to offer public or guest access safely without purchasing additional hardware. Some consumer and small-office wireless routers offer a guest access feature. When guest access is enabled, users will see another network name (known as an SSID) in the list of available networks on their Wi-Fi devices, and its access will be separated from the main network.
Business-class routers and access points (APs) typically offer multiple SSID and virtual LAN (VLAN) features. When these features are set up properly, multiple wireless network names (SSIDs) can be broadcasted with varying levels of security, one of which could be a guest network safely segregated from your private network.
Honeypot/honeynet
When talking about network security, honeypots and honeynets are often mentioned. Honeypots are a rather clever approach to network security but perhaps a bit expensive. A honeypot is a system set up as a decoy to attract and deflect attacks from hackers. The server decoy appears to have everything a regular server does—OS, applications, and network services. The attacker thinks he is accessing a real network server, but he is in a network trap.
The honeypot has two key purposes. It can give administrators valuable information on the types of attacks being carried out. In turn, the honeypot can secure the real production servers according to what it learns. Also, the honeypot deflects attention from working servers, allowing them to function without being attacked.
A honeypot can:
- Deflect the attention of attackers from production servers.
- Deter attackers if they suspect their actions may be monitored with a honeypot.
- Allow administrators to learn from the attacks to protect the real servers.
- Identify the source of attacks, whether from inside the network or outside.
One step up from the honeypot is the honeynet. The honeynet is an entire network set up to monitor attacks from outsiders. All traffic into and out of the network is carefully tracked and documented. This information is shared with network professionals to help isolate the types of attacks launched against networks and to proactively manage those security risks. Honeynets function as a production network, using network services, applications, and more. Attackers don’t know that they are actually accessing a monitored network.
Testing lab
Network segmentation is the act of splitting a computer network into subnetworks, each being a network segment, which increases security and can also boost performance. It is a security best practice that is recommended (but not required) by PCI DSS and it makes the top 20 list of critical security controls suggested by SANS.
Network segmentation will not keep an attacker from breaching your network, however it does limit a breach to one part of your network. Organizations who hold credit card information, financial information, research and development information, and any intellectual property on their network should properly segment off this data from the main network.
Load balancing
Network servers are the workhorses of the network. They are relied on to hold and distribute data, maintain backups, secure network communications, and more. The load of servers is often a lot for a single server to maintain.
This is where load balancing comes into play. Load balancing is a technique in which the workload is distributed between several servers. This feature can take networks to the next level; it increases network performance, reliability, and availability.
Performance optimization
All devices on the network, from routers to cabling, and especially servers, must have one prime underlying trait: availability. Networks play such a vital role in the operation of businesses that their availability must be measured in dollars. The failure of a single desktop PC affects the productivity of a single user. The failure of an entire network affects the productivity of the entire company and potentially the company’s clients as well. A network failure might have an even larger impact than that as new e-commerce customers look somewhere else for products, and existing customers start to wonder about the site’s reliability.
Every minute that a network is not running can potentially cost an organization money. The exact amount depends on the role that the server performs and how long it is unavailable. For example, if a small departmental server supporting 10 people goes down for 1 hour, this might not be a big deal. If the server that runs the company’s e-commerce website goes down for even 10 minutes, it can cost hundreds of thousands of dollars in lost orders.
The importance of data availability varies between networks, but it dictates to what extent a server/network implements fault tolerance measures. The projected capability for a network or network component to weather failure is defined as a number or percentage. Because no solution is labeled as providing 100 percent availability indicates that no matter how well you protect your networks, some aspect of the configuration will fail sooner or later.
In fault tolerance, RAID is only half the story. Measures are in place to cope with failures of most other components as well. In some cases, fault tolerance is an elegant solution, and in others, it is a simple case of duplication.
Disk-Level Fault Tolerance
Deciding to have hard disk fault tolerance on the server is the first step; the second is deciding which fault tolerance strategy to use. Hard disk fault tolerance is implemented according to different RAID levels. Each RAID level offers differing amounts of data protection and performance. The RAID level appropriate for a given situation depends on the importance placed on the data, the difficulty of replacing that data, and the associated costs of a respective RAID implementation. Often, the costs of data loss and replacement outweigh the costs associated with implementing a strong RAID fault tolerance solution. RAID can be deployed through dedicated hardware, which is more costly, or can be software-based. Today’s network operating systems, such as UNIX and Windows server products, have built-in support for RAID.
Compliance
So, how did a breach of this scale occur at a company that was compliant with PCI DSS? Apparently, malware installed on company servers intercepted card data as it was transmitted from cash registers to credit card processors. The malware then stored the purloined data on store computers before forwarding it to servers located offshore; from there it could be collected and used for fraudulent purposes (some 1,800 cases of such fraud were reported).
Some security-savvy consumers were quick to ask why the card data was not encrypted. The PCI standard, after all, generally requires card data to be encrypted when at rest or in transit over public networks. However, the guidelines do not specifically require encryption at the time of capture. Not surprisingly, since the incident came to light, Hannaford has started encrypting card numbers from the moment they are swiped at checkout counters. Many retailers already perform these actions as a best practice, although it is likely that many more currently do not.
Encryption on this scale can be expensive, both in terms of installation and of key management and maintenance, and even some security experts would agree that such a measure is overkill if certain other security measures are in place. The PCI DSS took this assumption into account. Contrary to some interpretations of the standard, PCI does not mandate encryption of card data at all times. In fact, the standard spells out how a company could avoid the use of encryption and still remain compliant through the use of “compensating controls” to protect data at rest. This approach is allowed “for companies unable to render cardholder data unreadable (for example, by encryption) due to technical constraints or business limitations.”
The basis for such compensatory controls is spelled out in Appendix B of PCI DSS version 1.1, which makes it clear that “Only companies that have undertaken a risk analysis and have legitimate technological or documented business constraints can consider the use of compensating controls to achieve compliance.” The standard goes on to make it clear that compensating controls consist of either a device or combination of devices, applications and controls that meet four very specific conditions:
1. Provide additional segmentation/abstraction (for example, at the network-layer)
2. Provide ability to restrict access to cardholder data or databases based on the following criteria:
- IP address/Mac address
- Application/service
- User accounts/groups
- Data type (packet filtering)
3. Restrict logical access to the database
- Control logical access to the database independent of Active Directory or Lightweight Directory Access Protocol (LDAP)
4. Prevent/detect common application or database attacks (for example, SQL injection).

Recent Comments