N10-007 Given a set of requirements, implement a basic network
Wireless Networks can be incorporated for a variety of networks in terms of shapes and sizes. Wireless Networks enable forming connection by using radio waves and not wires. Computers on wireless transceivers (transmitters and receivers) which are known as Access Point (AP) can move around in a premises and do need to be wired for use. Convenience, security and speed are some of the factors that have led to the development of these networks. Before we can understand how to implement a wireless network, it is important to understand wireless devices.
– Wireless Access Point: Wireless AP’s do the work of both a transmitter and a receiver for WLAN radio signals. It is a separate device with a built in:
- Antenna
- Transmitter
- Adapter
Access Points on a wireless network form a link between WLAN’s and a wired Ethernet LAN. They have the advantage of supporting multiple ports, which allows for expanding networks. One or more than one AP may be required depending on the size of the network. There is a range up to which an AP can send a usable signal. This distance is controlled by the wireless standard that has been adopted for setting up the network. This distance is also controlled by factors like obstructions and environmental conditions. The figure given below illustrates configuration of a wireless network
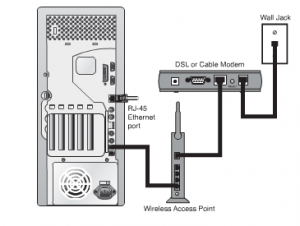
Figure 49: APs Connect WLANs and a Wired Ethernet LAN
An AP is an integral part of the wireless infrastructure network design. The network for which wireless set up is being used can be a private Ethernet network or the internet. The following are important to be understood for the working of an AP.
- Service Set Identifier (SSID): This network name is required to set up connection with a wireless AP. It is like a group name that is used by 802.11 wireless networks for all systems that belong to the same network. It is mandatory for client stations to be configured with SSID in order to be authenticated to the AP. The AP broadcasts the SSID to all the wireless clients. Systems can be configured in a manner, where the SSID is issued by the administrator rather than it being done automatically.
- Basic Service Set (BSS): BSS is a term that is used to denote wireless networks using single AP and one or multiple clients connecting to the AP. Home offices generally follow this design.
- Extended Service Set (ESS): The connection formed when two or more BSS sets are connected it is known as an ESS. It uses multiple AP’s. It is used for networks of a larger size. This permits the users to shift their position between BSS’s without having to reconfigure every time they move.
- Extended Service Set Identifier (ESSID): Though there is some basic difference between ESSID and SSID can be used in place of each other. In an ESS setup all AP’s may not be using the same name and it is the name given when ESS wireless network design is used. SSID is the name used with BSS networks.
- Basic Service Set Identifier (BSSID): The BSSID refers to the MAC address of the BSS AP. The BSSID is not to be confused with the SSID, which is the name of the wireless network.
- Basic Service Area (BSA): BSA is an important consideration when processes of troubleshooting or designing wireless networks have to be undertaken. It pertains to the coverage area of the AP. The BSA is controlled by multiple factors like the strength of the AP antenna, type of antenna and interference experienced in an area.
– Wireless Antennas: Wireless Communication cannot be imagined without wireless antennas. Depending upon the needs of the network the shape and size of the antenna has to be chosen. Selection of an antenna is an important factor while setting up a wireless network. The performance of the network depends to a great extent on the choice of antenna that has been made. The right antenna means saving on costs, better transmission, fewer antennas, and fewer access points. The basic tasks expected of an antenna are:
- To transmit around obstacles;
- Reduce the effects of interference;
- Enhance the strength of the signal and
- Enhance the speed of the signal.
Types of Wireless Antennas: It is important to understand the coverage used by an antenna before selecting the type of an antenna to be used. The wireless environment controls the choice of the antenna. Typically, antennas are:
- Omnidirectional: It is useful where wave degrees are to be dispersed in 360 degree pattern. It is best suited where coverage is required in all directions. These antennas are used when broad based signals are required. It allows access from multiple locations. The disadvantage with this type of antenna is the signal is not very strong and hence remains limited to smaller distances. Omnidirectional antennas are preferred for home and small offices.
- Directional: These antennas are used when signal is to be concentrated in one particular direction. It transmits a focused signal, meaning a greater distance can be traveled with stronger signals between two points. These are best suited for point to point configurations; as they travel greater distance. These are preferred when transmission needs to be tunneled through a series of obstacles. A chartered path helps to concentrate and strengthen the signal. The figure given below illustrates both directional as well as omnidirectional antennas.
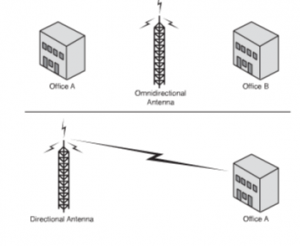
Figure 50: Directional Antenna Signal
Data Rate versus Throughput: Data rate and Throughput are independent factors though very often these are used interchangeably. Every wireless standard has a data rate associated with it. For example, the standard 802.11b, has a data rate of maximum 11Mbps. Data Rate is the maximum rate at which data travels in a given network. The speed that a network finally gains is controlled by multiple factors like clients on a network, error recovery data, obstructions etc. Collisions affect the ultimate data rate to a great extent.
After considering the impact of various factors, the data rate that is actually achieved is termed as throughput of data. The throughput hovers around half or even less than the data rate that is actually listed.
Setting up Communication between Wireless Networks
In case an infrastructure wireless network design is being used for setting up communication between two networks, the two key parts of the network are:
- The wireless client (known as the station or STA in short)
- The Access Point (AP in short) which acts as the bridge between the STA and the network.
The step that precedes transmission is communication between the wireless AP and the client. This initial step consists of
– Association: The moment a wireless adapter is turned on, the client adapter starts to scan for wireless AP’s or other wireless devices (in an ad hoc mode).
In the infrastructure mode the wireless AP can be chosen by the user. This exercise of choice can also be automated depending on the SSID, strength of the signal and error rate. Then the wireless adapter switches to the assigned channel of the wireless AP that has been selected. The AP negotiates the use of the port.
Every time the signal is dropped at a level below acceptability the adapter starts to scan for another AP with a stronger signal. The process is repeated with the new AP and is termed as re-association.
– Authentication: Once the association process gets over starts the process of authentication. The first step in authentication is application of keyed security measures. AP’s can be set for two kinds of authentication:
- Shared key authentication: In this the client has to deliver up to the security requirements before communication with AP can start.
- Open authentication: This is the default key setting and in this authentication enables access only with the SSID or /and with the WEP key. The shortcoming of this method is in case, the other protection or mechanism is not in place the system become vulnerable to intruders.
Once security requirements are complied with, IP level communication is established and Ethernet networking starts.
Many components are combined for setting up effective wireless communication between two devices. These components are required to be configured on both the client and the AP. These devices are:
- SSID/ESSID: These are required in both the cases – ad hoc as well as infrastructure. It is a client identification and essential while communicating with a particular base station.
- Wireless Channel (RF): It is also an important part of wireless communication. It refers to the band of frequency that is used while establishing wireless communication.
Security Features: Under the umbrella of 802.11 standards, security is provided fro by using two methods:
- Authentication
- Encryption
Beacon Management Frame
Within every wireless network is a frame type that is known as the beacon management frame (beacon). It is an integral and an important part of a wireless network. Its main job is to indicate the presence of the AP’s so that they can easily be located by the systems. These have the potential of being automatically detected by the wireless clients, which then try to establish wireless connection.
In an infrastructure design, the beacon frame is sent out by the AP and in case of ad hoc design, beacons are only sent out if they are connected. A beacon frame consists of different parts and all are used by the client frame to gather information about the AP. These parts are:
- Channel Information: This contains information about the channel used by the AP.
- Supported Data Rates: This contains information about the data transfer rates identified by the AP configuration.
- SSID: This contains the name of the wireless network name.
- Time Stamp: This contains Synchronization information. It is used by the client system to synchronize its clock with the AP.
A beacon is let out from the AP at an interval of every ten minutes. Since these add overheads to the networks, some AP’s increasing the time gap and hence reducing the number of beacons that are sent. Before connection can be made to an AP by a client system, the AP has to be located. This location can be detected actively or passively. After it is detected, the beacon frame provides the information necessary for the system to access the AP.
Configuring the Wireless Connection
While configuring, the first screen that one would come across is illustrated in the figure given below:
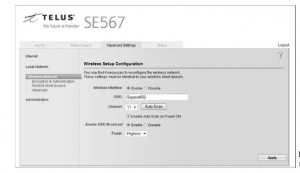
Figure51: Wireless Configuration Information
It is clear in the screen shot that settings for the wireless router are laid out. The connection is using an SSID password of Gigaset602 and channel as 11. All access points have similar configuration, though they may differ in the layout. Adjusting settings for troubleshooting or security reason can be done from the configuration screen. The settings used by an AP are:
– SSID: In the above screenshot, this configuration uses an SSID of Gigaset602. In a large network, this can be changed in order to facilitate identification of its locations or network segment. For the purposes of troubleshooting, it is essential to first ascertain that at both the ends the same SSID is being used. These may become incompatible when a computer is moved from one network to another. The system has to be rebooted to allow communication.
– Channel: In the above screenshot, the connection is set to use channel 11. For accessing this network, all systems would have to use this particular channel. A dropdown menu can be used to change the choice of channel.
– SSID Broadcast: In default settings, the SSID name is broadcast at fixed intervals. This permits the customers to discover the network. This also compromises on the important issue of security, as SSID’s are not encrypted.
– Authentication: Authentication can be done by using three options:
- WEP-open: This is simplest of three methods that can be used for authentication. It is a weak method and does not perform client verification.
- WEP-shared: This method requires that a WEP key be configured at both the ends. In this method authentication is mandatory. This system is relatively secure for wireless transmission.
- WPA-PSK: This is the strongest form of security available. In this method, keys are automatically changed and authenticated between devices. This is done after a specified period or after a specified number of packets has been transmitted.
– Wireless Mode: It is necessary that the client system use the identical wireless mode as the AP. Keeping the requirement of speed in mind, these days networks are configured 802 .11g or 802.1 1b/g as there is compatibility between the two.
– DTIM Period: Broadcasts can be made to all systems on a wireless network. Multicast or broadcast traffic refers to these multiple broadcast messages that are sent. The feature that all systems are awake to receive a broadcast message is termed as Delivery traffic indication message (DTIM). The settings of this particular feature specify how often the DTIM message is sent within the beacon frame. The default setting of this feature is 1. The setting 1 means that every beacon a DITM message will be sent.
– Maximum Connection Rate: The default setting for this feature is Auto. The auto setting permits maximum connection speed. The speed can be altered to enhance the distance that the signal covers and the strength of the signal.
– Network Type: This is where the choice between ad hoc or network is made.

Recent Comments