N10-007 Compare and contrast physical security controls
Mantraps
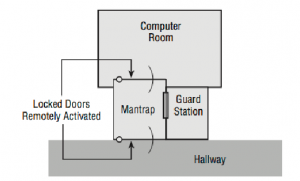
High-security installations use a type of intermediate access control mechanism called a mantrap (also occasionally written as man-trap). Mantraps require visual identification, as well as authentication, to gain access. A mantrap makes it difficult for a facility to be accessed by large numbers of individuals at once because it allows only one or two people into a facility at a time. It’s usually designed to contain an unauthorized, potentially hostile person physically until authorities arrive. Figure 68 illustrates a mantrap. Notice in this case that the visual verification is accomplished using a security guard. A properly developed mantrap includes bulletproof glass, high-strength doors, and locks. After a person is inside the facility, additional security and authentication may be required for further entrance.
FIGURE 68 – A mantrap in action
Video monitoring
In high-security and military environments, an armed guard as well as video surveillance would be placed at the mantrap. Beyond mantraps, you can combine guards with cameras (or even the threat of cameras) to create a potent deterrent. The cameras can send signals to a room where they are monitored by a guard capable of responding to a situation when the need arises.
Door access controls
Perimeter security, whether physical or technological, is the first line of defense in your security model. In the case of a physical security issue, the intent is to prevent unauthorized access to resources inside a building or facility.
Physical perimeter security is intended to accomplish for a network what perimeter security does for a building. How do you keep intruders from gaining access to systems and information in the network through the network? In the physical environment, perimeter security is accomplished through fencing, locks, doors, surveillance systems, and alarm systems. This isn’t functionally any different from a network, which uses border routers, intrusion detection systems, and firewalls to prevent unauthorized access.
Few security systems can be implemented that don’t have weaknesses or vulnerabilities. A determined intruder can, with patience, overcome most security systems. The task may not be easy, and it may require careful planning and study;
however, a determined adversary can usually figure out a way. This is why deterrence is so important.
If you want to deter intruders from breaking into your building, you can install improved door locks, coded alarm systems, and magnetic contacts on doors and windows. Remember that you can’t always keep an intruder out of your building; however, you can make an intrusion riskier and more likely to be discovered if it happens.
Proximity readers/key fob
Access control is a critical part of physical security, and it can help cut down the possibility of a social engineering or other type of attack from succeeding. Systems must operate in controlled environments in order to be secure. These environments must be, as much as possible, safe from intrusion. Computer system consoles can be a vital point of vulnerability because many administrative functions can be accomplished from the system console. These consoles, as well as the systems themselves, must be protected from physical access.
A key aspect of access control involves physical barriers. The objective of a physical barrier is to prevent access to computers and network systems. The most effective physical barrier implementations require that more than one physical barrier be crossed to gain access. This type of approach is called a multiple barrier system or defense in depth.
Ideally, your systems should have a minimum of three physical barriers:
- The external entrance to the building, referred to as a perimeter, which is protected by burglar alarms, external walls, fencing, surveillance, and so on. This should be used with an access list, which identifies who can enter a facility and who can be verified by a guard or someone in authority.
- A locked door protecting the computer center; you should also rely on such items as ID badges, proximity readers, fobs, or keys to gain access.
- The entrance to the computer room itself. This should be another locked door that is carefully monitored. Although you try to keep as many intruders out with the other two barriers, many who enter the building could be posing as someone they are not— heating technicians, representatives of the landlord, and so on. Although these pre- tenses can get them past the first two barriers, the locked computer room door should still stop them.
Biometrics
Biometric systems use some kind of unique biological trait to identify a person, such as fingerprints, patterns on the retina, and handprints. Some methods that are used include hand scanners, retinal scanners, facial recognition applications, and keystroke recognition pro- grams, which can be used as part of the access control mechanisms.
These devices should be coupled into security-oriented computer systems that record all access attempts. They should also be under surveillance in order to prevent individuals from bypassing them.
These technologies are becoming more reliable, and they will become widely used over the next few years. Many laptops sold now have a fingerprint reader built in. The costs associated with these technologies have fallen dramatically in recent years. One of the best independent sources of information on development in the field of biometrics is BiometricNews.net, where you can find links to publications and their blog.
Keypad/cipher locks
A lock refers to a number of types of device for securing a door. While there are combination locks, smart card locks, and keyed locks, the mechanism known as a cipher lock is opened with a programmable keypad and — according to definition — is not a true lock. There is also a specific type of cipher lock called a Cypher Lock®, which was developed by Continental Instruments, now a division of Napco Security Group.
The U.S. Army distinguishes the use of cipher locks and keyed locks, stating that the purpose of keyed locks is to maintain physical security, while the purpose of cipher locks is to control access, limiting either unannounced intrusions or unescorted entry to particular areas of a facility that are sensitive. Cipher locks are used to control access to areas such as airport control towers, computer rooms, corporate offices, embassies, areas within financial institutions, research and development laboratories, and storage areas holding weapons, controlled substances, etc.
A cipher lock may have four or five pushbuttons, depending on the manufacturer. Even with five pushbuttons, the code may be one to five digits. When the cipher lock unit is set up the code is programmed and shared with authorized personnel. It can be changed at any time.
Cipher locks are available in a variety of metallic colors and can be equipped with either a knob or a lever. The system may be mechanical, as is the case with the cipher locks made by Simplex or electronic, as is the Cypher Lock®. An electronic system allows for unlocking the door from a location within the room when a visitor who does not have the code arrives.
Security guard
A bank does not protect the money that it stores only by placing it in a vault. It uses one or more security guards as a first defense to watch for suspicious activities and to secure the facility when the bank is closed. It probably uses monitoring systems to watch various activities that take place in the bank, whether involving customers or employees. The vault is usually located in the center of the facility, and layers of rooms or walls also protect access to the vault. Access control ensures that the people who want to enter the vault have been granted the appropriate authorization before they are allowed access, and the systems, including manual switches, are connected directly to the police station in case a determined bank robber successfully penetrates any one of these layers of protection.
Networks should utilize the same type of layered security architecture. No system is 100 percent secure and nothing is foolproof, so no single specific protection mechanism should ever be trusted alone. Every piece of software and every device can be compromised in some way, and every encryption algorithm can be broken by someone with enough time and resources. The goal of security is to make the effort of actually accomplishing a compromise more costly in time and effort than it is worth to a potential attacker.

Recent Comments