N10-007 Given a scenario, implement network hardening techniques
Anti-malware software
Host-based anti-malware products have two components: a security agent that resides on the desktop and a central management server, or host. The agent detects threats such as viruses, spam and rootkits while it provides protection. The server portion manages and updates the agents and produces any necessary reports. Also included, depending on the product, are firewalls and host intrusion prevention solutions, or HIPS.
Other ways to provide protection from malware include gateway appliances that sit on a network perimeter or routers and switches with enhanced security. An example of an appliance is McAfee’s 3100 Secure Internet Gateway Appliance, which uses software and hardware to filter email and Web content for malware and unsafe Web sites. Cisco Systems has built security features into some of its routers and switches, which mitigate problems like denial of service attacks and IP phone call eavesdropping.
Switch port security
You can use the port security feature to limit and identify MAC addresses of the stations allowed to access the port. This restricts input to an interface. When you assign secure MAC addresses to a secure port, the port does not forward packets with source addresses outside the group of defined addresses. If you limit the number of secure MAC addresses to one and assign a single secure MAC address, the workstation attached to that port is assured the full bandwidth of the port. If a port is configured as a secure port and the maximum number of secure MAC addresses is reached, when the MAC address of a station that attempts to access the port is different from any of the identified secure MAC addresses, a security violation occurs. Also, if a station with a secure MAC address configured or learned on one secure port attempts to access another secure port, a violation is flagged. By default, the port shuts down when the maximum number of secure MAC addresses is exceeded.
DHCP snooping
DHCP snooping acts like a firewall between untrusted hosts and DHCP servers. You use DHCP snooping to differentiate between untrusted interfaces connected to the end user and trusted interfaces connected to the DHCP server or another switch. When a switch receives a packet on an untrusted interface and the interface belongs to a VLAN that has DHCP snooping enabled, the switch compares the source MAC address and the DHCP client hardware address. If the addresses match (the default), the switch forwards the packet. If the addresses do not match, the switch drops the packet.
ARP inspection
Dynamic ARP inspection is a security feature that validates ARP packets in a network. It intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from certain man-in-the-middle attacks.
Dynamic ARP inspection ensures that only valid ARP requests and responses are relayed. The switch performs these activities:
- Intercepts all ARP requests and responses on untrusted ports
- Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before it updates the local ARP cache or before it forwards the packet to the appropriate destination
- Drops invalid ARP packets
Dynamic ARP inspection determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On untrusted interfaces, the switch forwards the packet only if it is valid.
MAC address filtering
IP source guard is a security feature that filters traffic based on the DHCP snooping binding database and on manually configured IP source bindings in order to restrict IP traffic on non-routed Layer 2 interfaces. You can use IP source guard to prevent traffic attacks caused when a host tries to use the IP address of its neighbor. IP source guard prevents IP/MAC spoofing.
You can enable IP source guard when DHCP snooping is enabled on an untrusted interface. After IP source guard is enabled on an interface, the switch blocks all IP traffic received on the interface, except for DHCP packets allowed by DHCP snooping. A port ACL is applied to the interface. The port ACL allows only IP traffic with a source IP address in the IP source binding table and denies all other traffic.
The IP source binding table has bindings that are learned by DHCP snooping or are manually configured (static IP source bindings). An entry in this table has an IP address, its associated MAC address, and its associated VLAN number. The switch uses the IP source binding table only when IP source guard is enabled.
You can configure IP source guard with source IP address filtering, or with source IP and MAC address filtering. When IP source guard is enabled with this option, IP traffic is filtered based on the source IP address. The switch forwards IP traffic when the source IP address matches an entry in the DHCP snooping binding database or a binding in the IP source-binding table. When IP source guard is enabled with this option, IP traffic is filtered based on the source IP and MAC addresses. The switch forwards traffic only when the source IP and MAC addresses match an entry in the IP source-binding table.
Security policies
Without a security policy, the availability of your network can be compromised. The policy begins with assessing the risk to the network and building a team to respond. Continuation of the policy requires implementing a security change management practice and monitoring the network for security violations.
You can start with a general policy that covers all network systems and data within your company. This document should provide the general user community with an understanding of the security policy, its purpose, guidelines for improving their security practices, and definitions of their security responsibilities. If your company has identified specific actions that could result in punitive or disciplinary actions against an employee, these actions and how to avoid them should be clearly articulated in this document.
The next step is to create a partner acceptable use statement to provide partners with an understanding of the information that is available to them, the expected disposition of that information, as well as the conduct of the employees of your company. You should clearly explain any specific acts that have been identified as security attacks and the punitive actions that will be taken should a security attack be detected.
Lastly, create an administrator acceptable use statement to explain the procedures for user account administration, policy enforcement, and privilege review. If your company has specific policies concerning user passwords or subsequent handling of data, clearly present those policies as well. Check the policy against the partner acceptable use and the user acceptable use policy statements to ensure uniformity. Make sure that administrator requirements listed in the acceptable use policy are reflected in training plans and performance evaluations.
Use secure protocols
SSH
Secure Shell (SSH) is a protocol that provides a secure connection to a router. Cisco IOS supports version 1 of SSH, which enables clients to make a secure and encrypted connection to a Cisco router. Before SSH was implemented, the only form of security available when accessing devices such as routers was Telnet username/password authentication, which is clearly visible with a network sniffer. Telnet is insecure because a protocol analyzer can view the information in clear text form. Figure 2.14 displays a simple protocol analyzer viewing information between a source address, 10.66.32.5, and the destination address 192.168.1.13 after a Telnet session is initiated by the address (PC) 192.168.1.13/24.
SNMPv3
Application layer protocol, Simple Network Management Protocol (SNMP), is used to manage IP devices. SNMP is part of the TCP/IP application layer suite. SNMP allows network administrators the ability to view and change network parameters and monitor connections locally and remotely. Managing network performance over a period of time is one of the major functions that SNMP provides.
There are three version of SNMP:
- SNMP Version 1 (SNMPv1)
- SNMP Version 2 (SNMPv2)
- SNMP Version 3 (SNMPv3)
Both SNMPv1 and SNMPv2 use a community-based form of security. The community string allows access to the SNMP agent and can also be defined by an IP address access control list and password.
To set up the community access strings to permit access to the Simple Network Management Protocol (SNMP) on a Cisco IOS router, use the snmp-server community global configuration command:
snmp-server community string [view view-name] [ro | rw] [number]
TLS/SSL
TLS is the most widely deployed protocol for securing network traffic. It is widely used for protecting Web traffic and for e-mail protocols such as IMAP and POP. The primary advantage of TLS is that it provides a transparent connection-oriented channel.
Thus, it is easy to secure an application protocol by inserting TLS between the application layer and the transport layer. However, TLS must run over a reliable transport channel — typically TCP. It therefore cannot be used to secure unreliable datagram traffic.
However, over the past few years an increasing number of application layer protocols have been designed that use UDP transport. In particular protocols such as the Session Initiation Protocol (SIP) and electronic gaming protocols are increasingly popular. (Note that SIP can run over both TCP and UDP, but that there are situations in which UDP is preferable). Currently, designers of these applications are faced with a number of unsatisfactory choices.
First, they can use IPsec. However, for a number of reasons, this is only suitable for some applications. Second, they can design a custom application layer security protocol. SIP, for instance, uses a subset of S/MIME to secure its traffic. Unfortunately, although application layer security protocols generally provide superior security properties (e.g., end-to-end security in the case of S/MIME), they typically requires a large amount of effort to design — in contrast to the relatively small amount of effort required to run the protocol over TLS.
Overview of DTLS
The basic design philosophy of DTLS is to construct “TLS over datagram”. The reason that TLS cannot be used directly in datagram environments is simply that packets may be lost or reordered. TLS has no internal facilities to handle this kind of unreliability, and therefore TLS implementations break when re-hosted on datagram transport. The purpose of DTLS is to make only the minimal changes to TLS required to fix this problem. To the greatest extent possible, DTLS is identical to TLS. Whenever we need to invent new mechanisms, we attempt to do so in such a way that preserves the style of TLS.
SSL
Secure Socket Layer (SSL) is an encryption technology for web host devices used to provide secure transactions. For example, a secure transaction is required when clients enter their credit card numbers for e-commerce via their browser. When the end user enters a web address via an Internet browser, such as Internet Explorer, instead of entering HTTP: //web address in the address window, the end user enters HTTPS://web address.
Secure Hypertext Transfer Protocol secure site, or HTTPS, transports HTTP-based traffic over an SSL connection and provides a stronger authentication mechanism than HTTP.
HTTPS runs over TCP port 443. SSL is defined in RFC 2246.
The SSL Handshake Protocol was first developed by Netscape Communications Corporation to provide security and privacy over the World Wide Web. The SSL protocol supports server and client authentication. The SSL protocol is application-independent, allowing protocols like HTTP, FTP, and Telnet to be layered on top of it transparently. In other words, it is a session layer-based protocol. Cisco has developed a number of content-based switches to accelerate this communication, such as the Cisco SCA 11000 Series Secure Content Accelerator. The Cisco SCA 11000 Series Secure Content Accelerator is an appliance-based solution that increases the number of secure connections supported by a website by offloading the processor intensive tasks related to securing traffic with SSL.
HTTPS
The SSL Handshake Protocol was first developed by Netscape Communications Corporation to provide security and privacy over the World Wide Web. The SSL protocol supports server and client authentication. The SSL protocol is application-independent, allowing protocols like HTTP, FTP, and Telnet to be layered on top of it transparently. In other words, it is a session layer-based protocol. Cisco has developed a number of content-based switches to accelerate this communication, such as the Cisco SCA 11000 Series Secure Content Accelerator. The Cisco SCA 11000 Series Secure Content Accelerator is an appliance-based solution that increases the number of secure connections supported by a website by offloading the processor intensive tasks related to securing traffic with SSL. After an SSL session is established, no further authentication is required.
Access lists
Access Control List (ACL) are filters that enable you to control which routing updates or packets are permitted or denied in or out of a network. They are specifically used by network administrators to filter traffic and to provide extra security for their networks. This can be applied on routers (Cisco).
ACLs provide a powerful way to control traffic into and out of your network; this control can be as simple as permitting or denying network hosts or addresses. You can configure ACLs for all routed network protocols.
The most important reason to configure ACLs is to provide security for your network. However, ACLs can also be configured to control network traffic based on the TCP port being used.
Wireless security
Many different strategies and protocols are used to secure LAN and WAN transmissions. What about network transmissions that travel over the airwaves?
In the last few years, wireless networking has changed the look of modern networks, bringing with it an unparalleled level of mobility and a host of new security concerns.
WEP
Wired equivalent privacy (WEP) was the first attempt to keep wireless networks safe. WEP was designed to be easy to configure and implement. Originally, it was hoped that WEP would provide the same level of security to wireless networks as was available to wired. For a time it was the best and only option for securing wireless networks.
WEP is an IEEE standard introduced in 1997, designed to secure 802.11 networks. With WEP enabled, each data packet transmitted over the wireless connection would be encrypted. Originally, the data packet was combined with a secret 40-bit number key as it passed through an encryption algorithm known as RC4. The packet was scrambled and sent across the airwaves. On the receiving end, the data packet passed through the RC4 backward, and the host received the data as it was intended.
The two types of WEP security are static and dynamic. Dynamic and static WEP differ in that dynamic WEP changes security keys periodically, making it more secure. Static WEP uses the same security key on an ongoing basis.
The primary security risks are associated with static WEP, which uses a shared password to protect communications. Security weaknesses discovered in static WEP mean that WLANs protected by it are vulnerable to several types of threats. Freely available hacking tools make breaking into static WEP-protected wireless networks a trivial task. Unsecured WLANs are obviously exposed to these same threats as well; the difference is that less expertise, time, and resources are required to carry out the attacks. To continue the analogy, think of WEP security as a door knob that now has a lock added to it.
WPA/WPA2
Security weaknesses associated with WEP gave administrators a valid reason to be concerned about wireless security. The need for increased wireless security was important for wireless networking to reach its potential and to reassure those who had sensitive data that it was safe to use wireless communications.
In response, Wi-Fi Protected Access (WPA) was created. WPA was designed to improve on the security weaknesses of WEP and to be backward compatible with older devices that used the WEP standard. WPA addressed two main security concerns:
Enhanced data encryption: WPA uses a temporal key integrity protocol (TKIP), which scrambles encryption keys using a hashing algorithm. Then the keys are issued an integrity check to verify that they have not been modified or tampered with during transit.
Authentication: Using Extensible Authentication Protocol (EAP), WEP regulates access to a wireless network based on a computer’s hardware- specific MAC address, which is relatively simple to be sniffed and stolen. EAP is built on a more secure public-key encryption system to ensure that only authorized network users can access the network.
WPA2
The 802.11i standard provides for security enhancements to the wireless standard with particular focus on authentication. The standard is often referenced as WPA2, the name given it by the Wi-Fi Alliance. The difference between WPA and WPA2 is that the former implements most—but not all—of 802.11i to communicate with older wireless cards (which might still need an update through their firmware to be compliant) and it used the RC4 encryption algorithm with TKIP, whereas WPA2 implements the full standard and is not compatible with older cards.
TKIP/AES
Temporal Key Integrity Protocol (TKIP) was designed to address the shortcomings of the WEP security protocol. TKIP is an encryption protocol defined in IEEE 802.11i. TKIP was designed not only to increase security but also to use existing hardware, making it easy to upgrade to TKIP encryption. TKIP is built on the original WEP security standard but enhances it by “wrapping” additional code at both the end and the beginning of the data packet. This code modifies the code for additional security. Because TKIP is based on WEP, it too uses the RC4 stream encryption method. But unlike WEP, TKIP encrypts each data packet with a stronger encryption key than is available with regular WEP.
TKIP provides strong encryption for home users and nonsensitive data. However, it may not provide the level of security necessary to protect corporate or more sensitive data while in transmission.
802.1x
An IEEE security standard designed for authenticating wireless devices. This standard uses Extensible Authentication Protocol (EAP) to provide a central authentication server to authenticate each user on the network.
User authentication
PAP
Password Authentication Protocol provides security authentication mechanism for links. After the initial PPP link has been established the two-way handshake is used by the client to verify its identity. The main disadvantage of PAP is that the username and password are sent in clear text format. As PAP imposes security vulnerabilities into the network it is not supported now days.
Working of PAP
In case of PAP firstly the link is established then the user sends their username/password for authentication after the authentication is complete the session is allowed.
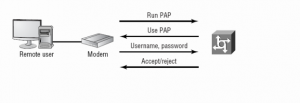
Figure 64: PAP Authentication
Challenge Handshake Authentication Protocol (CHAP)
It is more secure than PAP. The username and the password sent by CHAP are encrypted. CHAP checks the identity of the user after some interval periodically. It uses the three-way handshake to perform this functionality.
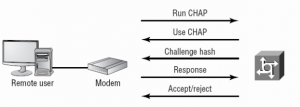
Figure 65: CHAP
MS-CHAP
It is the Microsoft version of CHAP called as MS-CHAP. It uses PPP authentication between a system running Microsoft operating system and NAS. There are several ways that the MS-CHAP differs from CHAP.
1) MS-CHAP response packets are compatible with Microsoft networking
products.
2) MS-CHAP is enables after link establishment.
3) MS-CHAP can allow the remote client to change the MS-CHAP password.
4) In case of failed session there are various code that why the link establishment failed and these codes are then returned to the remote client by the NAS.
EAP
Extensible Authentication Protocol via the LANs It is an authentication framework used in wireless networks. EAP can be used for wireless LANs as well as wired LANs. EAP is an authentication framework. There are various. It was developed to help two devices to negotiate. There are various types of EAP used today.
EAP-ESK
It is most popular form of authentication used in wireless networks. There is a shared key used between WAP and client. They are encrypted using powerful AES encryption.
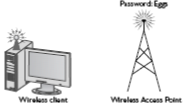
Figure 66: Wireless Client and Access point
EAP-TLS
EAP along with the transport layer security defines the use of RADIUS as well as authentication requiring certificates on the server and client. It is used primarily on wireless networks and TLS is used on the secure websites.
EAP-TTLS
It is similar to TLS but it uses only single server side certificates as in case of EAP-TLS certificates are used on both sides.
EAP-MS-CHAPv2
It is known as PEAP. It uses a password function based on MS-CHAPv2 with the addition of an encrypted TLS tunnel similar to EAP-TLS.
EAP-MD5
This is simple version of EAP that uses MD5 for the transfer of authentication credentials. EAP-MD5 is weak as compared to other EAP methods.
LEAP
It is called as Lightweight Extensible Authentication Protocol (LEAP). It is Cisco proprietary EAP authentication used by Cisco wireless devices. LEAP is a combination of MS-CHAP and RADIUS server.
Kerberos
Kerberos is an authentication and encryption method similar to RADIUS or TACACS+. It was developed at the Massachusetts Institute of Technology (MIT). It uses the same authentication mechanism as RADIUS and TACACS+ use the main difference is that after the user gets authenticated with Kerberos they are granted admission tickets. This ticket is used by the user to access various resources in the network without the need to enter their passwords again and again. The tickets that the Kerberos provides cannot be transferred or refunded. There is a limited time span of these tickets. After the admission ticket provided by the Kerberos has expired, the user needs to renew the ticket to access the network resources again. Kerberos is used by various devices. It is inbuilt in Windows 2000 and is implemented in Cisco routers. Until now it is the most secure method to authenticate the user.
Two-factor and Multifactor Authentication
When two or more access methods are included as part of the authentication process, you’re implementing a multifactor system. A system that uses any two items—such as smart cards and passwords—is referred to as a two-factor authentication system. A multifactor system can consist of a two-factor system, three-factor system, and so on. As long as there is more than one factor involved in the authentication process, it is considered a multifactor system.
For obvious reasons, the two or more factors employed should not be from the same category. Although you do increase difficulty in gaining system access by requiring the user to enter two sets of username/password combinations, it is preferred to pair a single username/password combination with a biometric identifier or other check.
Hashes
Several hashing algorithms are available.
Message hashing is an encryption technique that ensures a message or data has not be tampered with or modified.
MD5 Message hashing is supported on Cisco IOS routers. A variable-length message is taken, the MD5 algorithm is performed (for example, the enable secret passwords command), and a final fixed-length hashed output message is produced. MD5 is defined in RFC 1321.
Figure 66 displays the MD5 message operation.
Figure 66 MD5 Operations
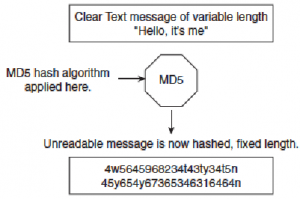
Figure 66 displays the simple clear text message, “Hello, it’s me,” which can be of any variable length. This message is sent to the MD5 process, where the clear text message is hashed and a fixed-length, unreadable message is produced. The data can include routing updates or username/password pairings, for example. MD5 produces a 128-bit hash output.
Secure Hash Algorithm (SHA) is the newer, more secure version of MD5, and Hash-based Message Authentication (HMAC) provides further security with the inclusion of a key exchange. SHA produces a 160-bit hash output, making it even more difficult to decipher. SHA follows the same principles as MD5 and is considered more CPU-intensive.
SHA
Several hashing algorithms are available. The two discussed here are MD5 and SHA (sometimes called SHA-1).
Message hashing is an encryption technique that ensures a message or data has not be tampered with or modified.
MD5 Message hashing is supported on Cisco IOS routers. A variable-length message is taken, the MD5 algorithm is performed (for example, the enable secret passwords command), and a final fixed-length hashed output message is produced. MD5 is defined in RFC 1321.
Figure 67displays the MD5 message operation.
Figure 67 MD5 Operations
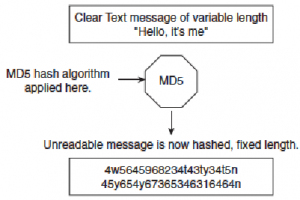
Figure 67 displays the simple clear text message, “Hello, it’s me,” which can be of any variable length. This message is sent to the MD5 process, where the clear text message is hashed and a fixed-length, unreadable message is produced. The data can include routing updates or username/password pairings, for example. MD5 produces a 128-bit hash output.
Secure Hash Algorithm (SHA) is the newer, more secure version of MD5, and Hash-based Message Authentication (HMAC) provides further security with the inclusion of a key exchange. SHA produces a 160-bit hash output, making it even more difficult to decipher. SHA follows the same principles as MD5 and is considered more CPU-intensive.

Recent Comments