N10-007 Differentiate between network infrastructure implementations
Multiple functions like easy communication, sharing of hardware, sharing of data and applications, easy storage and quick retrieval of data are expected from a network. The question in front of businesses these days is not whether to have a network or not but rather which form of network to choose.
Networks are categorized depending on the number of locations that they span. The options available are:
- LAN’s
- WAN’s
- MAN’s
- PAN’s
LAN: The full form of LAN is Local Area Network. This type of network caters to only a single location. It is built up with networking media that is fast, with the limitation that it caters to only a limited geographical area. The figure given below illustrates a LAN.
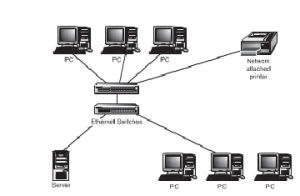
Figure 39: Local Area Network
WAN: The full form is Wide Area Network. This type of network caters to multiple geographic locations. These are slower and more costly than the local area networks. They work by connecting LAN’s to create an Internetwork.
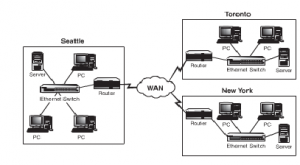
Figure 40: Wide Area Network
A WAN is a network that spans more than one geographic location often connecting separated LANs. WANs are slower than LANs and often require additional and costly hardware such as routers, dedicated leased lines, and complicated implementation procedures. Figure 1.2 shows an example of a WAN.
Occasionally, a WAN will be referenced as a Metropolitan Area Network (MAN) when it is confined to a certain geographic area, such as a university campus or city. No formal guidelines dictate the differences between a MAN and a WAN; technically, a MAN is a WAN. Perhaps for this reason, the term MAN is used less frequently than WAN. If any distinction exists, it’s that a MAN is smaller than a WAN. A MAN is almost always bigger than a LAN and usually is smaller than or equal to a WAN. MANs use an Internet service provider (ISP) or telecommunications (telco) provider.
PAN: The full form of this form of network is Personal Area Network. This form of network is associated with individuals. Wireless technologies are the most common use of PAN and are known as WPAN, that is, Wireless Personal Area Network. The term WPAN refers to technologies connecting devices which are closely placed to exchange data or resources. They use short-range wireless technology as the devices are placed in proximity. Infrared and Bluetooth are the examples of the same.
SCADA/ICS
Today’s major industries rely on finely automated industrial control sectors and are operated by critical infrastructures of highly interconnected and mutually dependent systems known as industrial control systems (ICS). These are predominantly found in industries such as transportation, electric, oil and natural gas, utility power, pulp and paper, mining, discrete manufacturing (i.e. durable goods, automotive, aerospace, etc.), chemical, metals, food and beverage, water and wastewater, and pharmaceutical.
The term ICS comprises three main types of systems which include distributed control systems (DCS), supervisory control and data acquisition (SCADA) systems, along with the incorporation of smaller controller hardware components such as the skid-mounted Programmable Logic Controllers (PLC).
DCS are usually found within a localized area, such as an industrial process plant or a factory, as a specific functional distributed control system design that relies on supervisory and regulatory control. DCS emerged as a tool for controlling the systems involved beyond a small cell area, while collecting data in real time on high-bandwidth/low-latency data networks. Because everything operates in real time, loop control will commonly extend up to the DCS top level controllers. Such systems can be found in refineries and chemical plants, among others.
SCADA systems were designed to cater to distribution applications where remote data must be gathered through more unreliable data networks, such as those with low-bandwidth/high-latency links. These systems are implemented in widely separated geographical sites (often scattered over thousands of square kilometers) using an open-loop control, through centralized data acquisition and supervisory control. Supervisory data is typically sent back to a control center through remote terminal units (RTUs), which tend to be restricted to a limited capacity for handling local controls whenever the master station is not available. With technological advances, however, the capability of these RTU systems continues to grow, allowing for better performance. SCADA systems are normally used in water pipelines and natural gas industries, to name a few.
PLCs are computer-based devices and are the result of the technological replacement of relay racks in ladder form. They are the primary components in small control system configuration and are used in almost all discrete industrial processes. PLCs are commonly integrated into DCS architectures as key components that provide feedback or feed forward control loops which automatically maintain the desired conditions of a process around a specific set point. Here, the PLC settings are specified to determine the desired tolerance and provide the rate of self- regulation and self-correction whenever there is a system upset.
Today, the boundaries are blurring between these three system definitions as current ICS architectures are evolving into hybrids that integrate features of both SCADA systems and DCS.
The key components for the operation of an ICS include: a control loop, Human-Machine Interface (HMI) and Remote Diagnostics and Maintenance Utilities.
The main control components of an ICS encompass: a control server, a SCADA Server or Master Terminal Unit (MTU), Remote Terminal Units (RTUs), Programmable Logic Controllers (PLCs), Intelligent Electronic Devices (IEDs), a Human-Machine Interface (HMI), a Data Historian and an Input/output (IO) Server
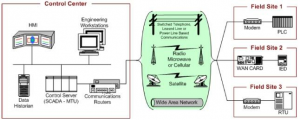
Figure 41: SCADA system general layout (NIST 800-82)
Control networks have merged with corporate networks in order to facilitate monitoring and controlling systems from the outside, which allows decision-makers at an enterprise level have access to process data. Network topologies can vary greatly from ICS to another, with different characteristics for each layer within a control system hierarchy, but the most important components they must include are: a
fieldbus network, a control network, communications routers, a firewall, modems, and remote access points.
Originally, ICS used specialized hardware and software to run proprietary control protocols, making them completely isolated systems with little resemblance to traditional information technology (IT) systems. However, in order to facilitate remote access capabilities and corporate connectivity, IT solutions are being designed and implemented into ICS. The use of standard computers, operating systems (OS) and network protocols, along with low-cost Internet Protocol (IP) devices to replace proprietary solutions, provides new IT capabilities, but reduces the ICS isolation from the outside world, thus increasing the possibility of cyber security vulnerabilities and incidents. Despite the availability of solutions to deal with these security issues in typical IT systems, special considerations and precautions must be tailored to secure the ICS. Additionally, efficiency and safety goals can sometimes conflict with security in the design and operation of control systems. Because each one of these ICS is unique in its performance and reliability, each one requires its own unique, and sometimes unconventional, operating system and applications which might be regarded as odd or challenging by typical IT personnel.
The implementation of an ICS always involves some form of impact, which is complex and can go far beyond the immediate processes at hand. Some of the ICS characteristics differ from traditional information processing systems because they affect the physical world directly. These might risk human and environmental health and safety, as well as detonate financial issues related to production losses which can compromise proprietary information and even have a negative impact on a country’s economy.
Medianets
To support these combined requirements and characteristics, Cisco is developing a suite of networking technologies that span the range of video-optimized products and define the medianet – an intelligent network optimized for rich media.
The following medianet technologies can be applied to enhance the SLAs offered for transported video services, individually or in combination, allowing broadcasters and service providers to choose the optimal set of capabilities to meet their video service requirements.
Fabric-Based Multicast Replication
Efficient multicast replication is fundamental to supporting point-to-multipoint video services such as video contribution. The Cisco video-optimized platforms use innovative service-intelligent switching fabrics built for massive multicast replication and forwarding, which provide superior in-fabric replication compared to products that use inefficient line-card-based replication.
Multi-Priority DiffServ Schedulers
The Cisco DiffServ IP/MPLS QoS implementation is mature and very widely deployed in the industry. Cisco has led the industry in developing multiple priority-scheduling implementations that have been optimized through focused development and years of experience supporting premium services, including video. These implementations provide end-to-end jitter of less than 1 ms in high-speed multiservice IP/MPLS networks as described in the following document:
- Clarence Filsfils and John Evans, “Deploying Diffserv in IP/MPLS Backbone Networks for Tight SLA Control,”
The following study demonstrates that these SLAs are achievable in high-speed multiservice IP/MPLS networks today; worst-case jitter was measured at less than 700 microseconds for probes sent at 1 Mbps during a 7-day period between the U.S. East- and West-coast POPs of a Tier-1 IP network service provider.
- Steve Casner, Cengiz Alaettinoglu, Chia-Chee Kuan, “A Fine-Grained View of High-Performance Networking,” Packet Design, NANOG 22, May 20-22, 2001
Fast IP-Routing Protocol Convergence
In IP networks, convergence is the process by which routing protocols find alternative paths around failed network elements (links or nodes). Cisco leads the industry in the development of implementation and protocol optimizations such as IP prefix prioritization, which can reliably deliver significantly sub-second network convergence times for unicast routing protocols such as Open Shortest Path First (OSPF), Intermediate System to Intermediate System (IS-IS), and Border Gateway Protocol (BGP), and for multicast routing protocols such as Protocol Independent Multicast (PIM).
- Pierre Francois, Clarence Filsfils, John Evans and Olivier Bonaventure, “Achieving sub-second IGP convergence in large IP networks,” ACM SIGCOMM Computer Communication
As a specific example, for 400 multicast groups, convergence times of about 200 ms are realistically achievable today with optimized implementations.
Fast Convergence may be enhanced with other technologies where faster recovery from failures is required, for premium video transport services.

Recent Comments