
Mantraps High-security installations use a type of intermediate access control mechanism called a mantrap (also occasionally written as man-trap). Mantraps require visual identification, as well as authentication, to gain access. A mantrap makes it difficult for a facility to be accessed by large numbers of individuals at once because it allows only one or two people into a facility at a time. It’s usually designed to contain an unauthorized, potentially hostile person physically until authorities arrive. Figure 68 illustrates a mantrap. Notice in this case that the visual verification is…

Anti-malware software Host-based anti-malware products have two components: a security agent that resides on the desktop and a central management server, or host. The agent detects threats such as viruses, spam and rootkits while it provides protection. The server portion manages and updates the agents and produces any necessary reports. Also included, depending on the product, are firewalls and host intrusion prevention solutions, or HIPS. Other ways to provide protection from malware include gateway appliances that sit on a network perimeter or routers and switches with enhanced security. An example…

Attacks/threats The main purpose of these attacks is to disable and corrupt the network services. This attack crashes the system or makes it too slow to be working efficiently. DOS attacks are very easy to perform and the main target of these attacks is the web servers. The primary purpose of these attacks is to deny access to the device or network by continuously bombarding the network with useless traffic. The DOS attack is started by the attacker by deploying Zombie programs in various computers that have a very high…

Disaster recovery Disaster Recovery is undertaken when the fault tolerance measures fail. Backups and Backup strategies form the essentials parts of disaster recovery. Backup Methods: There are several backup methods that can be chosen from. The choice of the method that is used for backup is controlled by the needs of the organization and the time that is available in which the backup must be taken. Backup is undertaken through a window and conducting the same outside the window tends to slow down the server. The different backup methods that…
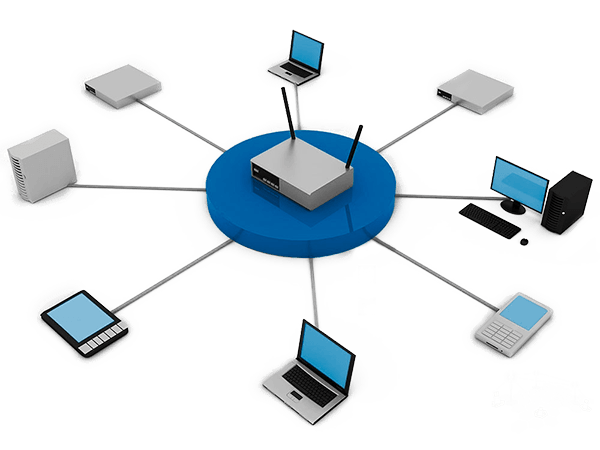
Small office/home office wireless router A small office/home office (SOHO) network is typically defined as one that serves 1 to 10 users; although, no hard and fast rule exists for this. The commonality between all implementations falling into this category is that usually a small number of users exist, and the physical environment is typically small. A number of SOHO-labeled solutions are available, including small routers and firewalls. Appropriately, a SOHO router typically serves 1 to 10 users on the system. Just as when configuring any other type of network,…
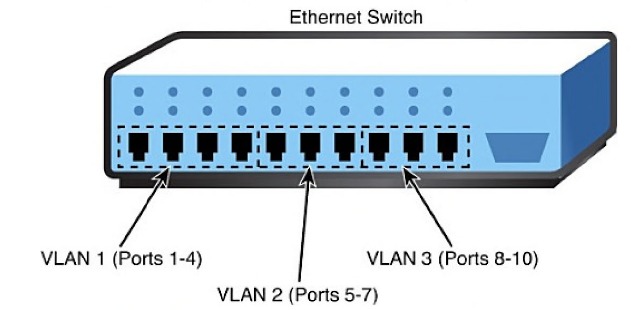
VLAN This is a group of connected computers that act work in the same manner as they would in their own network segments. This model creates logical segments of a network as a result the administrator enjoys greater amount of flexibility beyond the physical design and infrastructure. It allows better management as the network is classified in sections. This model allows isolation of segments and hence is a more secure model. The advantages of this model are: It ensures an enhanced level of security. It reduces traffic that passes through…

Windows Patch Management There’s no such thing as a perfect operating system, and Windows is no exception. From the moment Microsoft releases a new version of Windows, malware attacks, code errors, new hardware, new features, and many other issues compel Microsoft to provide updates, known more generically as patches in the computing world, to the operating system. The process of keeping software updated in a safe and timely fashion is known as patch management. Microsoft has been a leader in the process of patch management for decades. Microsoft’s primary distribution…

SCADA systems/Industrial control systems SCADA (supervisory control and data acquisition) is an industrial control system at the core of many modern industries such as manufacturing, energy, water, power, transportation and many more. SCADA systems deploy multiple technologies that allow organizations to monitor, gather, and process data as well as send commands to those points that are transmitting data. Virtually anywhere you look in today’s world, you will find some version of a SCADA system running, whether it’s at your local supermarket, refinery, waste water treatment plant, or even your own…

Archives/backups Even the most fault-tolerant networks can fail, which is an unfortunate fact. When those costly and carefully implemented fault-tolerance strategies fail, you are left with disaster recovery. Disaster recovery can take many forms. In addition to disasters such as fire, flood, and theft, many other potential business disruptions can fall under the banner of disaster recovery. For example, the failure of the electrical supply to your city block might interrupt the business functions. Such an event, although not a disaster per se, might invoke the disaster recovery methods. Full…

Baseline In the simplest terms, a network performance baseline is a set of metrics used in network performance monitoring to define the normal working conditions of an enterprise network infrastructure. Engineers use network performance baselines for comparison to catch changes in traffic that could indicate a problem. Setting a network baseline also provides early indicators that application and network demands are pushing near the available capacity, giving the networking team the opportunity to plan for upgrades. Aligning network performance baselines with existing network service-level agreements (SLAs) can help the IT…











Recent Comments